Answers
Answer:
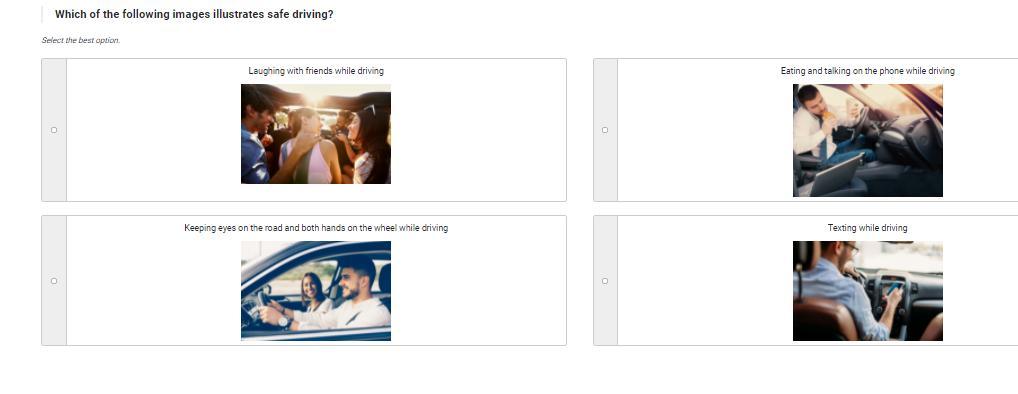
bottom left
Explanation:
Answer:
keep your eyes on the road!!!!
Related Questions
Select the correct answer from each drop-down menu.
Complete the following sentences.
_________ effort is an important and necessary factor for the success of any project. In software development projects,
_______team members carry out several tasks to ensure the quality of the process and the final product.
Options for the first box are: managers, A teams, an individuals
Options for the second box are:internal, specific, external
Answers
Answer:
First, A teams, Second ,Specific
Explanation:
You are working on a ticketing system. A ticket costs $10. The office is running a discount campaign: each group of 5 people is getting a discount, which is determined by the age of the youngest person in the group. You need to create a program that takes the ages of all 5 people as input and outputs the total price of the tickets. Sample input: 55 28 15 38 63 sample output: 42.5 the youngest age is 15, so the group gets a 15% discount from the total price, which is $50 - 15% = $42.5
Answers
Answer:
Explanation:
The following program is written in Java. It takes 5 inputs of int values for the ages of each member in the group. Then it loops through all of the ages and chooses the youngest age. Finally, it applies that age as a discount to the final price which would be $50, outputting the final discounted price. The output for the test case provided can be seen in the attached picture below in red.
import java.util.Scanner;
class Brainly
{
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
int[] person = new int[5];
System.out.println("Enter age of individual 1: ");
person[0] = in.nextInt();
System.out.println("Enter age of individual 2: ");
person[1] = in.nextInt();
System.out.println("Enter age of individual 3: ");
person[2] = in.nextInt();
System.out.println("Enter age of individual 4: ");
person[3] = in.nextInt();
System.out.println("Enter age of individual 5: ");
person[4] = in.nextInt();
int youngest = person[0];
for (int x = 0; x < person.length; x++) {
if (person[x] < youngest) {
youngest = person[x];
}
}
double discount = 1 - (((double)youngest) / 100);
double output = 50 * discount;
System.out.println("Total Price: " + output + " the youngest is " + youngest);
}
}
Consider the classes below: Which of the following statements is true? Group of answer choices The value of counter will be different at the end of each for loop for each class. The value of j will be the same for each loop for all iterations. Both The value of counter will be different at the end of each for loop for each class and The value of j will be the same for each loop for all iterations are true. Neither The value of counter will be different at the end of each for loop for each class nor The value of j will be the same for each loop for all iterations is true.
Answers
Answer:
probly
Explanation:
Both The value of counter will be different at the end of each for loop for each class and The value of j will be the same for each loop for all iterations are true.
No links it’s just a normal question about iPhones.
If you have someone in your contacts you talk with a lot but like everyday you delete the conversation multiple times will you stop receiving texts from that person even if you text them and it says delivered?
Answers
Answer:
You will still get the messages. You are just deleting the messages from YOUR device not the other persons, in order to stop recieving messages from the person you block them. In order to stop receving notifications, you put them on DND. But, if you talk to them everyday I would assume you would not want to stop receiving messages from them.
What requirements are necessary in order for you to share a file?
Check all that apply.
You own it.
You commented on it.
You can edit.
You know about the topic of the document.
Answers
Answer:
I. You own it.
II. You can edit.
Explanation:
A file can be defined as a computer resource that avails end users the ability to store or record data as a single unit on a computer storage device.
Generally, all files are identified by a name and type such as audio, image, video, document, system, text, etc. Each type of files can be transferred or send from one computer node to another computer node through the use of a wired or wireless connection and with the necessary level of permission.
The requirements which are necessary in order for you to share a file are;
I. You must own the file. This simply means that you have the authority to share the file and have it saved on your device.
II. You have the permission or required credentials to edit the file. A read-only permission cannot be used to edit a file but a full permission can be used.
write examples of hacking in internet?
Answers
Answer:
Although hacking is very bad, it can be found everywhere and anywhere.
Examples: Phishing, password checking, and keyloggers
Explanation:
Explanation:
Hacking is an attempt to exploit a computer system or a private network inside a computer. Simply put, it is the unauthorised access to or control over computer network security systems for some illicit purpose.
To better describe hacking, one needs to first understand hackers. One can easily assume them to be intelligent and highly skilled in computers. In fact, breaking a security system requires more intelligence and expertise than actually creating one. There are no hard and fast rules whereby we can categorize hackers into neat compartments. However, in general computer parlance, we call them white hats, black hats and grey hats. White hat professionals hack to check their own security systems to make it more hack-proof. In most cases, they are part of the same organisation. Black hat hackers hack to take control over the system for personal gains. They can destroy, steal or even prevent authorized users from accessing the system. They do this by finding loopholes and weaknesses in the system. Some computer experts call them crackers instead of hackers. Grey hat hackers comprise curious people who have just about enough computer language skills to enable them to hack a system to locate potential loopholes in the network security system. Grey hats differ from black hats in the sense that the former notify the admin of the network system about the weaknesses discovered in the system, whereas the latter is only looking for personal gains. All kinds of hacking are considered illegal barring the work done by white hat hackers.